ClickFix malware now targeting Mac users with fake CAPTCHA tricks

newYou can now listen to Fox News!
Clickfix, the social engineering tactic that targets both Windows and Mac users since early 2024, continues to develop.
Only last month, I reported how the attackers used Develop Windows users to install harmful programs themselves.
Now, the same trick is turned against McCos. Cyber security researchers have discovered a new campaign using CLICKFIX to introduce MacOS Stealer atomic (AMOS), which are strong harmful programs that are preparing for Australian programs targeting Apple systems.
Discover fake stores online, avoid fraud in Facebook
Explanation of the infiltrators at work. (Cyberguy “Knutsson)
What are Clickfix programs, and how do you work?
Security researchers in Cloudsek It has identified a new threat targeting MacOS users through imitation and deception. The campaign uses a technology known as Clickfix to attract victims with false online verification claims. This time, the attackers sabotage the spectrum, a major communications provider in the United States. They use the fraudulent areas similar to the real support gates. These include misleading titles such as Net Net Net and Spectrum Ticket.
Visitors to these sites are displayed on the standard captcha box, asking them to check their identity. When they do it, the site displays a fake error message that captcha failed. Users are encouraged to click a button called “alternative checking”. This leads to copying something silently copied to the portfolio. What happens after that depends on the user operating system. On McCosGuidelines for the user to paste and run the command at the station. This is actually a Shell text program designed to steal information and download harmful programs.
The text program is especially dangerous because it uses the orders of the legitimate MacOS system. He asks about the system password, harvested accreditation and disruption Security protection. Then he downloads Amos. This is the stealing of known information with a date for targeting Apple devices. Magistical programs collect sensitive data such as passwords, cryptocurrencies, automatic browser data and reserved cookies.
The researchers believe that the campaign was created by Russian -speaking attackers. The clues include comments written in the Russian language within the malware symbol. Analysts also indicated that the delivery infrastructure was poorly assembled. Uncomfortable instructions appeared across the devices. For example, Linux users have been shown Windows orders. Mac users were told to press the keys only on Windows devices.
Subscribe to the free Cyberguy report
Get my best technical advice, urgent safety alerts, and exclusive deals that are connected directly to your inbox. In addition, you will get immediate access to the ultimate survival guide – free when joining.
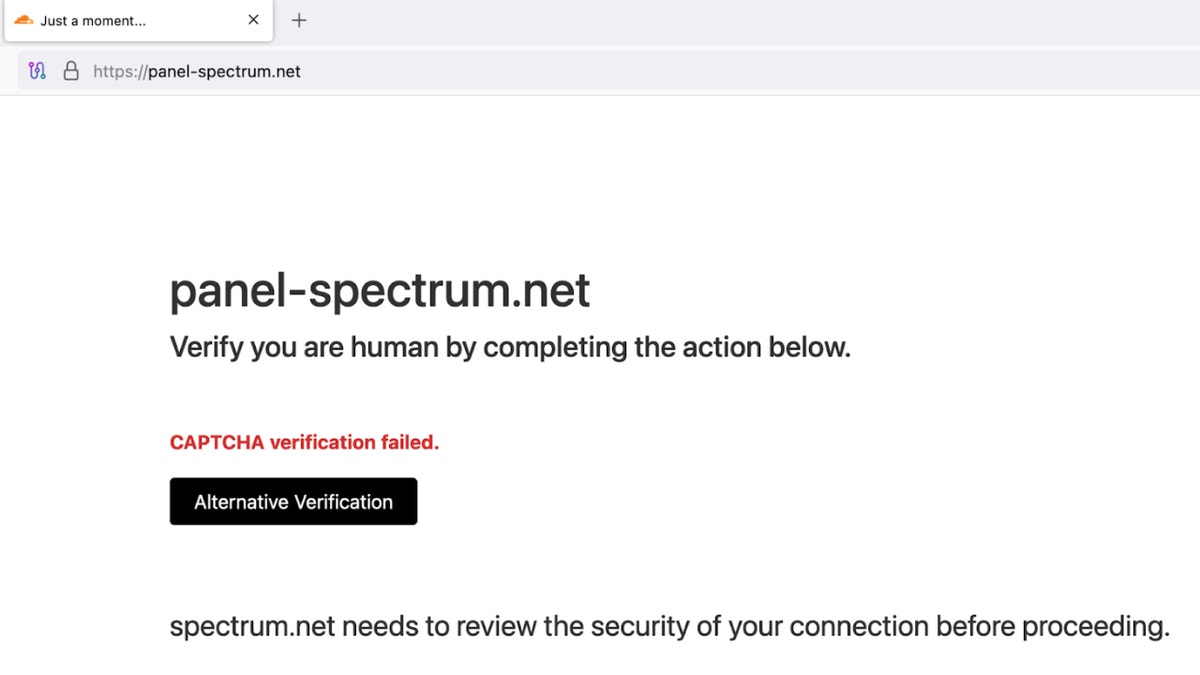
Captcha fake on Mac. (CloudSek)
Snements who outperform your identity stealing
Why clickfix attacks are very effective
Clickfix is the social engineering method that has gained popularity quickly Among the Internet criminals. It depends on users who trust what they see and follow simple instructions. In this campaign, the attacker’s goal is to make the victim implement the same infection process. Once the user follows, the system is penetrated without the need for traditional exploitation.
Researchers believe that Clickfix has been active since March 2024 at least. The attackers used fake error messages From Google Chrome, Microsoft Word and OneDrive to pay their loads. The victims were offered to “repair” claims, which have copied harmful in Powershell to their portfolio. Then they were directed to paste and operation in Powershell or through the Run dialog box.
By November 2024, the method developed more. A A new wave of attacks targeting Google Meet UsersStarting with deceptive emails that mimic internal meetings. These emails contained links to the fake landing pages designed to look like they came from the Special Victim Organization.
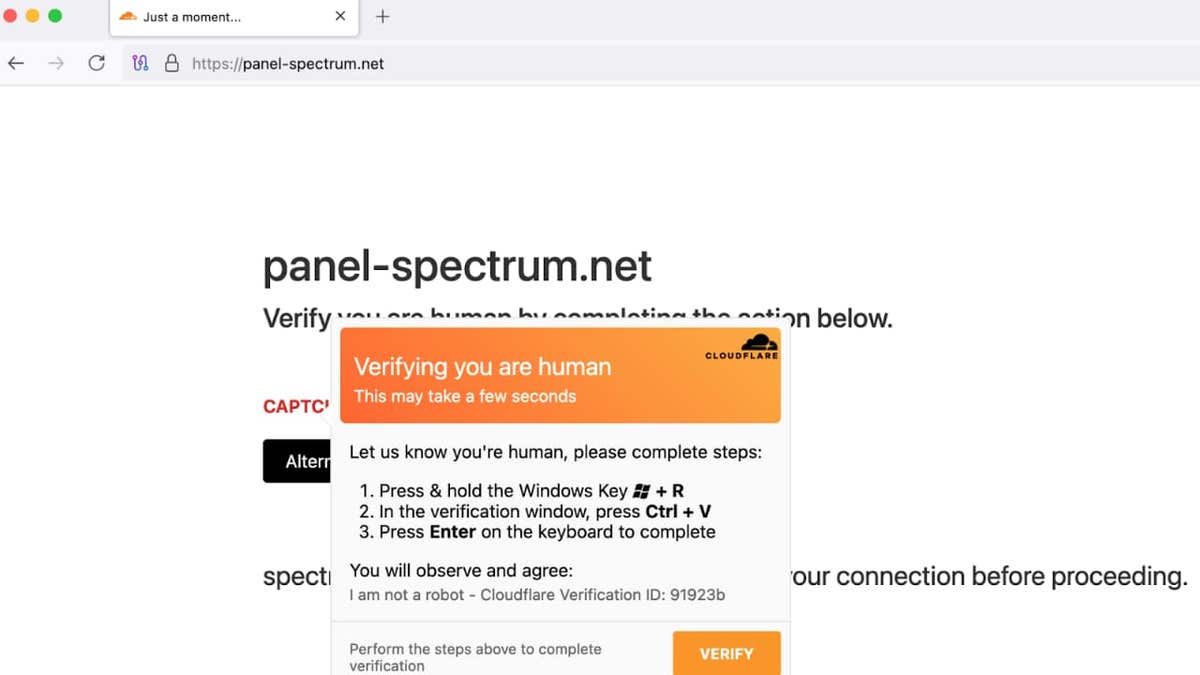
Captcha fake on Mac. (CloudSek)
Mescape programs display 3.9 billion passwords in the threat of huge cybersecurity
6 ways to protect yourself from Clickfix and similar harmful programs
To protect yourself from the advanced threat of Clickfix Malware, which continues to target users through advanced social engineering tactics, consider implementing these six basic security measures:
1. Be skeptical of CAPTCHA claims: Captcha tests never requires paste anything into a station. If the website guides you to do so, this is likely to be a fraud. Close the page immediately and avoid interacting with it.
2. Do not click on links from unspecified emails and use strong anti -virus programs: Several Clickfix attacks also start with deceptive emails that are apporating reliable services such as Booking.com or Google Meet. Always check the sender before clicking on the links. If it seems an urgent or unexpected email, go directly to the company’s official website instead of clicking on any links inside the email.
The best way to protect yourself from malicious links that prove harmful programs, which may reach your own information, is to install a strong antivirus program on all your devices. This protection can also be alerted to relieving emails and fraud on Ransomwari, and maintaining your personal information and digital assets. Get my choices for the best winners to protect antivirus 2025 for Windows, Mac, Android and iOS devices.
3. Enabling dual -factors authentication: maybe Dual factors authentication Whenever possible. This adds an additional layer of safety by requesting another form of verification, such as a code that is sent to your phone, as well as your password.
Get Fox Business on the Go by clicking here
4. Keep updated devices: regularly Update the operating system, browser and safety program It ensures that you have the latest stains against known gaps. Cybercrimins takes advantage of outdated systems, so automatic updates enable a simple but effective way to stay protected.
5. Monitor your accounts of suspicious activity and change your passwords: If you have interacted with a suspicious website, email for hunting, or a fake login page, check your online accounts for any unusual activity. Find unexpected login attempts, unauthorized password, or financial transactions that you do not recognize. If anything looks, change the passwords immediately and inform the activity to the relevant service provider. Also, consider using a Password Director To create and store complex passwords. Get more details about my country The best password managers reviewed by experts in 2025 here.
6. Invest in the personal data removal service: Think about using a service that monitors your personal information and alerts you to possible violations or unauthorized use of your data. These services can provide early warning marks to steal identity or other harmful activities or similar attacks. Although there is no service to remove all of your data from the Internet, get a great order removal service if you want to monitor and automate the process of removing your information from hundreds of sites continuously over a longer period of time. Check the best data removal choices here.
Get on Free examination To find out if your personal information has already gone out on the web
The massive security defect displays the most popular browsers on Mac
Court Kisa Curt
Experienced users can be deceived when malicious behavior is hidden as routine. The attack not only used a security vulnerability in MacOS, but also your knowledge of verification flows. As long as security instructions appear to be part of the usual experience, people will continue to operate the malicious code themselves. Mac users, like anyone else, need to deal with every familiar -looking interface with more doubts. Especially when you ask your password.
Click here to get the Fox News app
Do you think technology companies are doing enough to stop malicious programs like Clickfix? Let’s know through writing to us in Cyberguy.com/contact.
For more technical advice and security alerts, participated in the free newsletter of Cyberguy Report by going to Cyberguy.com/newsledter
Ask Court a question or tell us about the stories you want to cover.
Follow Court on his social channels
Answers to the most asked Cyberguy questions:
New from Court:
Copyright 2025 Cyberguy.com. All rights reserved.




