How hackers are breaking into Apple devices through AirPlay

AirPlay is designed from Apple to make life easier, allowing users to flow music, photos and videos from iPhone and MacBooks to TVs, loudspeakers and other devices that are compatible with only a click. But now, cybersecurity researchers revealed that this same comfort may open the door to the infiltrators. A new set of weaknesses, which are called air -portable, can convert tools that support air to surreptitious entry points for harmful programs and network.
Join the free “Cyberguy Report”: Get expert advice experts, critical safety alerts and exclusive deals, as well as immediate access to my country free “The ultimate survival guide “ Upon registration.
A person with an iPhone (Cyberguy “Knutsson)
What you need to know
Researchers at the Cyber Security Company, based in Tel Aviv Oligo newly Detected Airborne, a group of security defects in the Apple Airplay Protocol. These errors are found primarily in the AirPlay software development group (SDK) used by manufacturers to external parties to provide AirPlay support to smart TVs, loudspeakers and other media devices. It means safety defects if the infiltrator on the same Wi-Fi network as a weak device, they can kidnap it without touching the device.
From there, the attackers can move sideways within a network or network network, and jump silently from one device to another. They may install malware, ransom programs, disable operations, or even lock users from their own systems. In some cases, at risk devices can be added to robots, a network of kidnapped machines that work in complete harmony for larger attacks. Because many smart tools come with microphones, infiltrators can turn them into eavesdropping and monitoring tools.

A woman passed on her smartphone (Cyberguy “Knutsson)
200 million records for social media were leaked in the main X data breach
What does Apple do about air portable insects?
Apple has already corrected air mobile errors on its own devices and issued updates for third -party sellers. However, researchers warn that many of the third -party products that support air, and perhaps tens of millions, may never receive a solution, either because they do not keep automatically or because sellers are slow or unwilling to launch safety spots.
An amazing demonstration by Oligo showed how easy the Bose amplifier is to display the company’s logo, proving how easy the pirates are silently. Although Bose was not specifically targeted, the example highlights the wider risks. Any non -disorganized device with AirPlay SDK can be a gateway for harmful actors.
The researchers also discovered that Apple Carplay is affected. Despite its exploitation, it will be difficult, and the pairing requires Bluetooth or USB, more than 800 styles for cars and trucks may be weak.
HERTZ data breach displays customer information
How to update your iPhone program
- Go to Settings
- handle general
- Click Program update
- Download and install Last update.
- Your iPhone will Restart as soon as the update is completed.
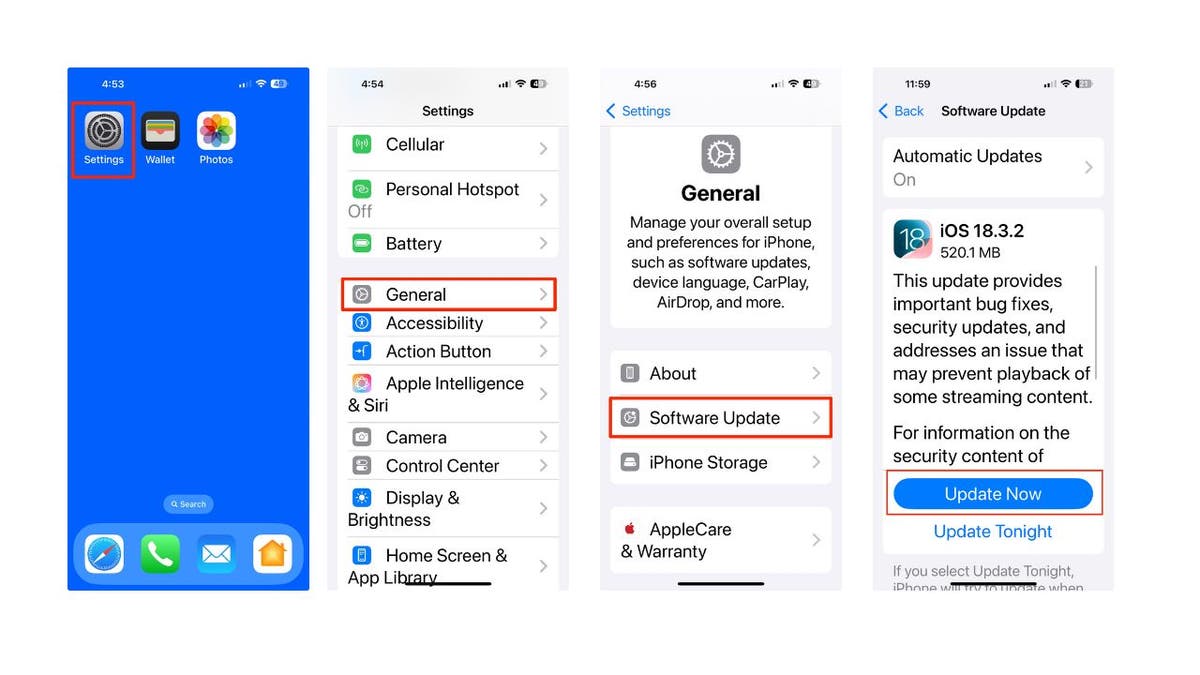
Steps to update your iPhone (Cyberguy “Knutsson)
How to update all your devices and keep them safe
5 ways to protect yourself from broadcasters
1) Separate Wi-Fi Settock for smart devices: Most modern routers allow you to create multiple networks. Use this feature to maintain your smart home appliances such as loudspeakers, TVs or AirPlay receptions on the “IOT of Things” network. Keep this separation from your main devices, such as phones, laptops and computers. This retail guarantees that even if the infiltrator gets a weak smart device, he will not be able to easily access more important or sensitive devices on the basic network.
2) Disable the broadcast when it is not used actively: AirPlay is always designed and discovered, which makes it comfortable but also leaves it exposed. If you rarely use AirPlay or use it only from time to time, go to your device’s settings and extinguish it completely. On Apple devices, AirPlay settings can be found under “General” or “AirPlay & Handoff”. For third -party devices, verify applications or accompanying evidence. AirPlay turning off is removed by an open kebab for attackers.
3) Avoid using AirPlay on the general or unprecedented Wi-Fi network and use VPN: One of the main conditions for air-to-air exploitation is that the attacker should be on the same Wi-Fi network as the target device. This makes the general Wi-Fi networks in places such as cafes, airports, hotels, or joint work spaces are especially fraught with risks. If you need to use your device in such environments, avoid casting, flowing, or associated with smart devices.
Consider using VPN to protect from infiltrators on your device as well. VPNS will protect you from those who want to track your potential site and the websites you visit. VPN is reliable necessary to protect your online privacy and ensure a safe and high -speed connection. For the best VPN The program, see experts review for the best VPNS to browse your web on Windows, Mac, Android and iOS devices.
4) Strengthening and securing the Wi-Fi home network: Make it difficult for attackers to reach your home network. Use a strong and unique password for Wi-Fi that is different from your other account adopting data. Make sure to update your router’s fixed program and that the encryption is set on WPA2 or WPA3. Avoid older and less safe options such as WeP or open networks. Turn off features like WPS, which are designed for easy preparation but can make your network more likely. If possible, disable the global connection and operation (UPNP) and the similar features that make all devices on your network easily detected. Also, consider using a password manager to create and store complex passwords. Get more details about my country The best password managers reviewed by experts in 2025 here.
5) Reducing device permissions and exposure: Broadcasting smart devices often include features such as microphones, automatic driving and remote access. Review the settings of each device and disable any features that you do not actively use. For example, if the smart speaker has a microphone, but you have never used voice commands, turn off the microphone or cover it. The more jobs revealed by the device, the greater the opportunities that the infiltrator must exploit. If your router supports it, use the rules of the protection wall at the device level to reduce services or communications online that smart tools can reach.
Court Kisa Curt
Apple loves to market itself as for privacy and safety, but air portable weaknesses show that the company’s devices are far from being gunfire. While they corrected their own products, millions of AirPlay third -party AirPlay are still open to the attack. It has become clear that Apple’s control over its ecological system is not tight as they wish to believe you. If they really want to be the leader of privacy, they must advance and fix these problems in all fields, not only when it suits them.
Do you trust the Apple claims about privacy and safety after reading this article? Let’s know through our writing in Cyberguy.com/contact.
For more technical advice and security alerts, participated in the free newsletter of Cyberguy Report by going to Cyberguy.com/newsledter.
Ask Kurt a question or tell us about the stories you want to cover.
Follow Court on his social channels:
Answers to the most amazing Cyberguy questions:
New from Court:
Copyright 2025 Cyberguy.com. All rights reserved.




%20teaser%20SOURCE%20Nothing.jpg?w=390&resize=390,220&ssl=1)