New phishing attack uses real-time interception to bypass 2FA

Holding attacks everywhere, most of us can discover clear attacks. Even if a person falls for one and delivers his password, the 2FA (2FA) authentication usually adds a decisive layer of protection. However, the new hunting group that makes tours can exceed 2FA fully by using the kidnapping of the session and intercepting dependence in the actual time.
This tool known as Astaroth is known, and it deals with traffic between your device and legitimate authentication services such as Gmail, Yahoo and Microsoft. Since it holds everything in the actual time, it completely exceeds 2FA and gives the attackers full access to your account.
Clarification of a drunk at work (Cyberguy “Knutsson)
How to work asaroth
Astaroth is a collection of the next level that transmits fraud to a completely new level. Instead of using the basic fake login pages such as traditional clinic groups, it works as mediators between your device and real authentication service while seizing everything that you need silently.
The attack begins when clicking on the hunting link and landing on a harmful site that looks identical to the real site. Since the site contains valid SSL certificates, there are no red flags, no security warnings, and there are no popup. When entering your login details, including the username, password, device information and IP address, Astaroth takes it before transferring the request to the actual site.
Dual factors authentication It is not a problem for stubbornness. It intercepts one -time passwords and the second that was entered, whether they are applying authentication, text messages, or payment notice. The stolen codes are immediately sent to the attacker through a web panel or a cable alert, so that they can use them before their validity.
The real Kicker is that Astaroth also holds cookies to the session, which are small parts of data that keep users registered after approval. The attackers can pump these cookies in their own browsers, and the need to completely overlooks passwords or authentication of the worker. Once they have the session, they are in any additional steps required.
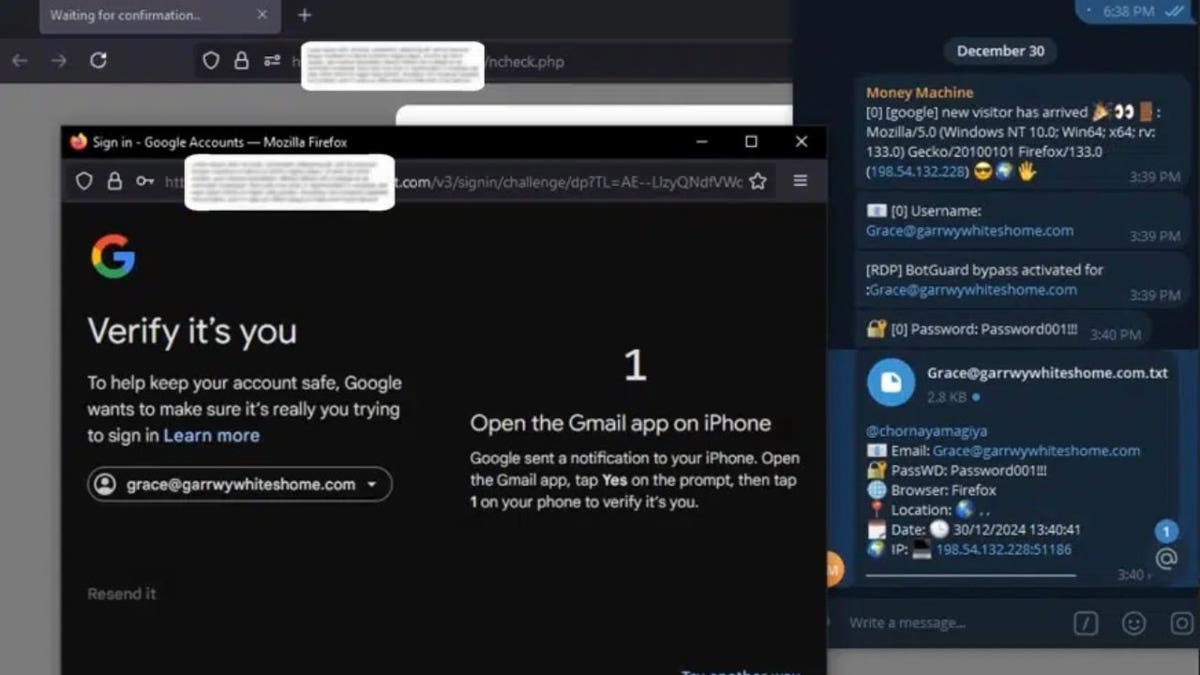
An example of what the victim and striker will see (Cyberguy “Knutsson)
The best antivirus for Mac, PC, iPhone and Androids viruses – Cyberguy Operations
Astaroth is shockingly advanced
As the Cyber Security Company mentioned SlashnextAstaroth is highlighted by other clinic groups because of their ability to intercept accreditation data in actual time, automate attacks and resist removal efforts. Traditional hunting depends on the deception of victims to enter their reliance on fake login pages, but Astaroth removes this step completely.
Besides its advanced capabilities, Astaroth comes with features that make it attractive to electronic criminals. Anti -lead hosting is used to stay online despite law enforcement efforts, and receives frequent updates to bypass safety corrections and follows an organized payment form. For $ 2000, buyers get six months of continuous promotions. To build confidence, even creators allow infiltrators to test the pre -purchase group.
Astaroth is widely available through Telegram and Enderground CRIME CRIME. Not to be identified by these platforms makes it difficult for the authorities to track the distribution.
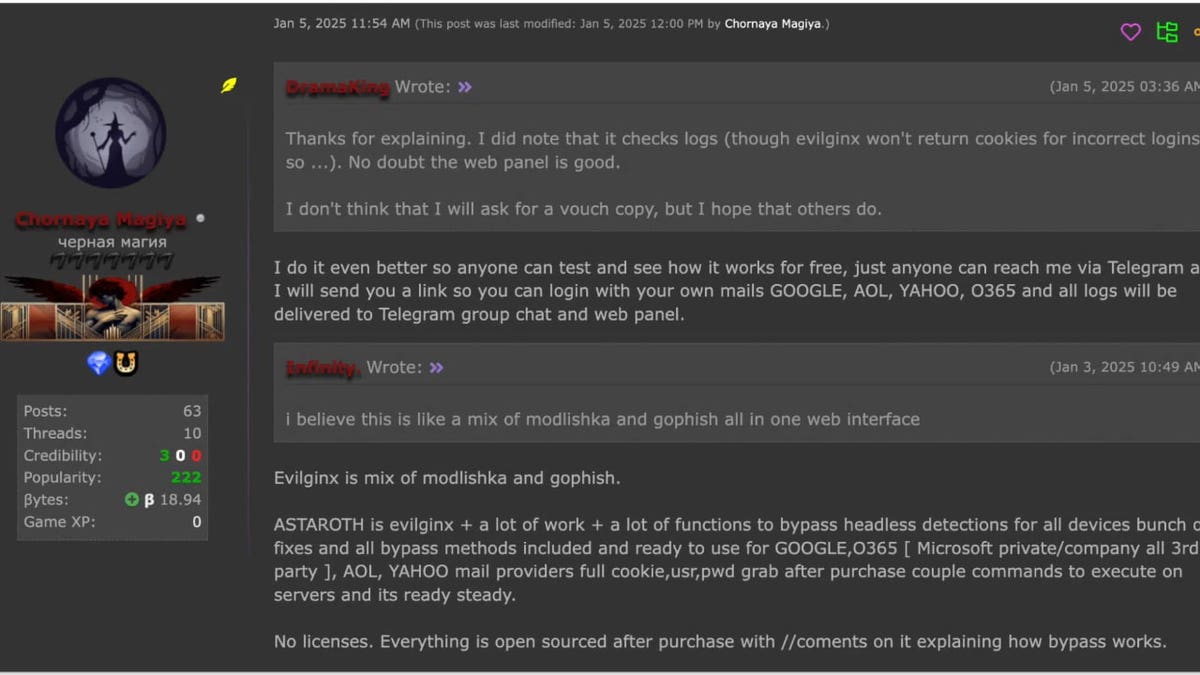
The seller shares the information about the scraps tested tester (Slashnext) (Cyberguy “Knutsson)
How to protect your data from this tax department’s contents this season
Signs may be infected
1) Unexpected account records or security alerts
- You receive alerts from Gmail, Microsoft or other services about logging in from an unknown device or location
- You get a 2FA request when you don’t try to log in
2) You are registered in mysterious circumstances of the accounts
- If the cookies are stolen in your session, the attacker may log in as you are and forcing the login elsewhere
3) Password changes or settings updates that you did not make
- If the attacker has a console, they may change emails, phone numbers, or passwords
4) Performing slow system or strange behavior
- Astaroth uses legitimate Windows (such as WMIC and Bitsadmin or RGSVR32) to hide itself
- If your system is slow or the task manager shows strange operations using the high central/network processing unit without any explanation, this may be an idea
5) The browser behaves strange
- Automatic login fields on automatic or incorrect episodes or redirects
- Pages that were working suddenly lead to warnings or errors
6) Uncommon programs or programs that work in the background
- Check for individual scheduled tasks, registry changes or background network connections (especially if they are outside the suspicious ranges or IPS).
What to do if you suspect infection
- The Internet immediately separated
- Do a full examination of harmful programs Use Virus reliable programming
- Check the unauthorized login On your main accounts and Change all passwords On another reliable device
- Empowering corridors or device safety keys Wherever it is possible
- Take your device If harmful programs continue; There may be a need to reset the full factory
- Monitor bank accounts and email funds For suspicious activity
4 Ways to stay safe from the Atstarted hunting attacks
1) Avoid unknown links and use strong antivirus programs: Remember that regardless of the progress of malware, it still needs inputs from you. In most cases, the attacker will be asked to click on a link before they can steal your data. For example, in order to work asarush, you must click on a link, visit a harmful web site and enter your credentials. If you do not click on the link, you will remain evident from malware.
The best way to protect yourself from malicious links that prove harmful programs, which may reach your own information, is to install a strong antivirus program on all your devices. This protection can also be alerted to relieving emails and fraud on Ransomwari, and maintaining your personal information and digital assets. Get the best winners of the Windows 2025 virus protection protection for Windows, Mac, Android and iOS.
2) Double sites: Always check the website addresses and use reference signals for reliable sites. Instead of clicking on links in emails or messages, type URL manually or use a reliable reference signal. This reduces the risk of landing on a fraudulent page designed to imitate a legitimate website.
3) Update your devices: You may wonder how to maintain update your devices against harmful programs such as Astarch. Although it does not prevent the attack directly, it ensures that the situation does not get worse. Keep your operating system and applications updated With the latest safety corrections, the weaknesses that harmful programs may be used, making it difficult for attackers to obtain a foothold on your device.
4) Avoid writing passwords: Avoid entering passwords whenever possible to reduce the risk of credit theft. Instead, use authentication methods such as corridors, log in to Google or log in to Apple.
A The corridor key It is a feature that uses encryption pairs to check your identity, and eliminate the need for traditional passwords. Log in to applications and websites allows you to use the same process that you use to unlock your device, such as biological measurements, pin or style.
Google Log in It is an advantage that allows you to log in to external applications or web sites using their Google account adoption data. It simplifies the login process by eliminating the need to create and remember user names for each service. You can log in with the “login with Google” button, login to Google or automatic login if it is previously authorized.
Apple registration It is a feature that enables you to log in in particular to the applications of the external parties and the participating websites using your Apple ID. It provides a quick, easy, and more special way to ratify without the need to create new accounts or mention additional passwords. To prepare an “login with Apple” account, when you ask you a website or a participant application to prepare or upgrade an account, do the following: Click Log in with Apple. Follow the instructions on the screen. Some applications (and web sites) do not request your name and email address. In this case, you can simply be authenticated with the face identifier or touch ID (depending on your form), then start using the application. Others may request your name and email address to prepare a dedicated account. When the application asks for this information, log in with the Apple your name and the personal email address from your Apple account to review it.
These methods depend on the encryption keys or safe symbols, which makes it difficult for the attackers to intercept your login information, even if they can deceive you to visit a harmful site.
The FBI’s warning of the dangerous “Smorish” fraud that targets your phone
Court Kisa Curt
Astaroth is shown to what extent the fishing groups came, taking things beyond the usual tricks and easily exceeding 2FA. It is a reminder that regardless of our safety, there are our systems, there is always a more intelligent attack pending the exploitation of gaps. Internet criminals adapt quickly, and although traditional defenses may not interrupt them anymore, there are still steps that you can take to respond: using login recordings without a password, staying updated and continued to identify these advanced threats.
What do you think that governments and companies do to protect you from advanced internet threats such as the ISARTARTS Group, which can go beyond traditional security measures? Let’s know through our writing in Cyberguy.com/contact.
For more technical advice and security alerts, participated in the free newsletter of Cyberguy Report by going to Cyberguy.com/newsledter.
Ask Kurt a question or tell us about the stories you want to cover.
Follow Court on his social channels:
Answers to the most amazing Cyberguy questions:
New from Court:
Copyright 2025 Cyberguy.com. All rights reserved.




